
Before we discuss Blackhole Lists (RBLs), we need to cover some background information regarding email security on a VPS with cPanel. One of the first things a cPanel user should learn is how to block spam in cPanel with DNS records and prevent your emails from being marked as junk. Many guides cover a lot of automated technical controls that can stop more obvious spam. But it’s not enough.
Phishing has been a top three most reported breach method for the last five years, according to Verizon’s 2020 Data Breach Investigation Report (DBIR). That means more needs to be done to mitigate phishing and other Business Email Compromise (BEC) attacks. And there undoubtedly are cyber attackers who know how to spam with cPanel or bypass these controls.
Blocking IP addresses from emailing your web server is another technical control to improve email security. WebHost Manager (WHM) allows multiple methods for this. The easiest is by country and domain. But with virtual private networks (VPNs) and proxy services (some free) being commonly used to bypass region restrictions, there’s still a lot of room for improvement.
A Real-time Blackhole List (RBL), or DNSBL, can help.
What is a Real-time Blackhole List (RBL)?
Sometimes used interchangeably with blacklist, a RBL is a list of IP addresses and domains that are known or suspected to be used for malicious purposes. That includes multiple factors:
- Newly registered domains
- IPs with a bad DNS reputation
- IPs sending emails with faulty headers
Your specific needs determine what types of RBLs and how many you should use. Remember, the biggest advantages to implementing RBLs are:
- You don’t have to manually maintain the list
- The work is done before it reaches the end user
Where are RBLs?
There are multiple 3rd party RBLs available online. WHM includes Spamhaus.org and SpamCop.net by default. For additional RBLs, check out Talos Intelligence IP blacklist and SpamEatingMonkey. Only enable one RBL within a few hours to help you spot and troubleshoot any legit emails being blocked. Auditing your Exim logs can help you troubleshoot false positives as well.
Remember, these are third party vendors. Research what these vendors do with the information they receive and requirements to use their blacklists before implementing their databases with your email server environment.
How to Add a Custom RBL in WHM
Below we’ll cover how to add a custom RBL in WHM. We’ll use the SpamEatingMonkey Black RBL in our example but the steps in WHM are the same for any others you find elsewhere.
- Log into WHM.
- On the left, select Exim Configuration Manager.
- Select the RBLs tab.
- Select Manage Custom RBLs.
- Under Add a new RBL, for Rbl Name, create a name that will help you identify it.
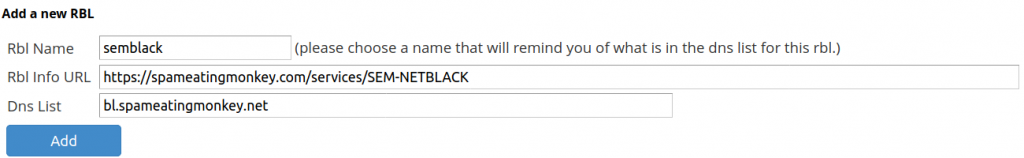
- (Optional) Add a Rbl Info URL for a webpage that provides additional information about the database.
- Add the actual RBL link for Dns List.
- Select Add to be taken to a notification page directing you to enable it in your Configuration Editor, then rebuild your Exim config.
- Select Configuration Editor to return to Manage Custom RBLs.
- Select RBLs.
- To right of Custom RBL: [YourNewRBL], select On.
- Select Save to rebuild Exim.
Again, adding Real-time Blackhole Lists is just one of many ways to mitigate, not prevent, phishing attacks. There are many other ways to harden your managed VPS or dedicated server. Security awareness training is required to fight more clever phishing and social engineering attacks such as the “On this day I hacked your OS” scam email. Let us know what RBLs you use to protect your email server below.
Learn more about managing cPanel accounts with with Managed VPS Hosting Product Guide.
Comments
It looks like this article doesn't have any comments yet - you can be the first. If you have any comments or questions, start the conversation!